
CMMC & Security Training
Your People are Your first line of defense…
and your weakest Link

Ultimate Defense for Cyber Attacks
From cybersecurity threats to regulatory requirements, organizations must address information security. Security awareness training is a key component of an information security program. You could argue that people are your first line of defense, but also your weakest link. One click by your employees, intentional or unintentional, can bypass your entire corporate IT security architecture. In addition to training, having the ability to test employees’ security awareness helps determine an organization’s efficacy when it comes to information security.
Cybersecurity Training
Phishing testing and other cybersecurity training is a continuous process of testing and remediation training. With these services, organizations can implement a comprehensive security awareness training program using a suite of security tools. For CMMC we do provide the current required training such as Annual Security Training, Insider Threat, CUI and job specific training as needed.
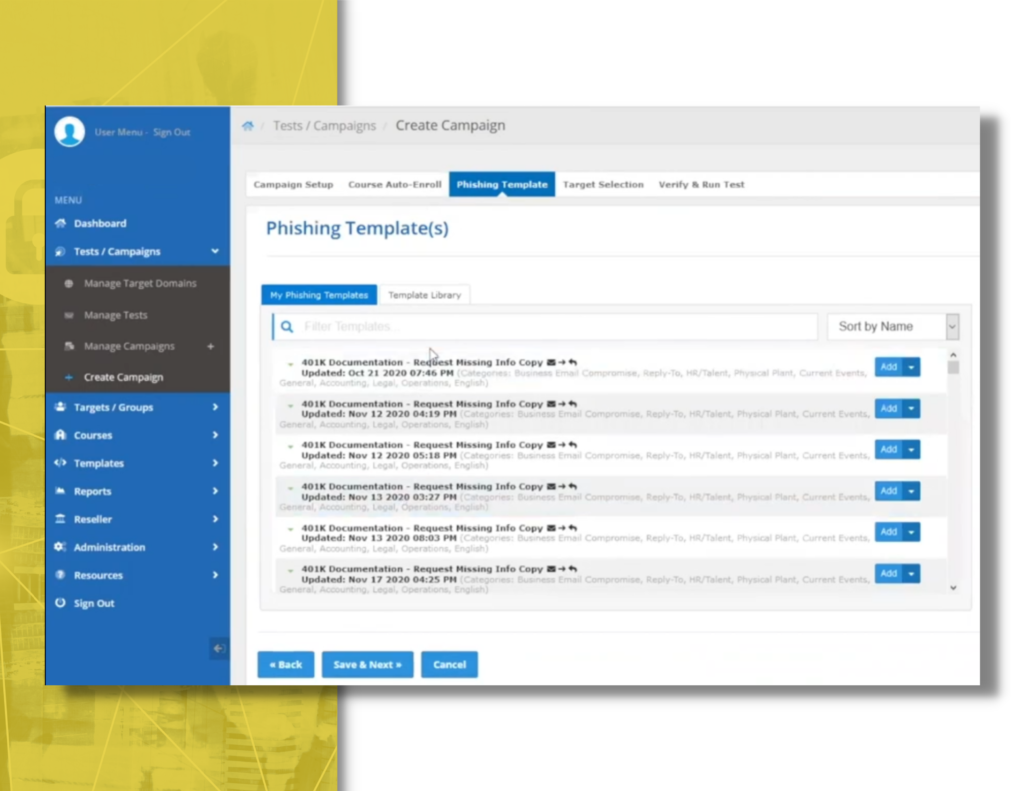
Learning Management System
We provide an integrated and compliant Learning Management System (LMS) to deliver training to users when they need it. It includes evidence/cert collection to make sure you have the necessary documentation ready for your audit. Our technology or processes can integrate with HR systems, manage policy acknowledgement and any CUI documentation your staff, contractors and suppliers will need to have in place.

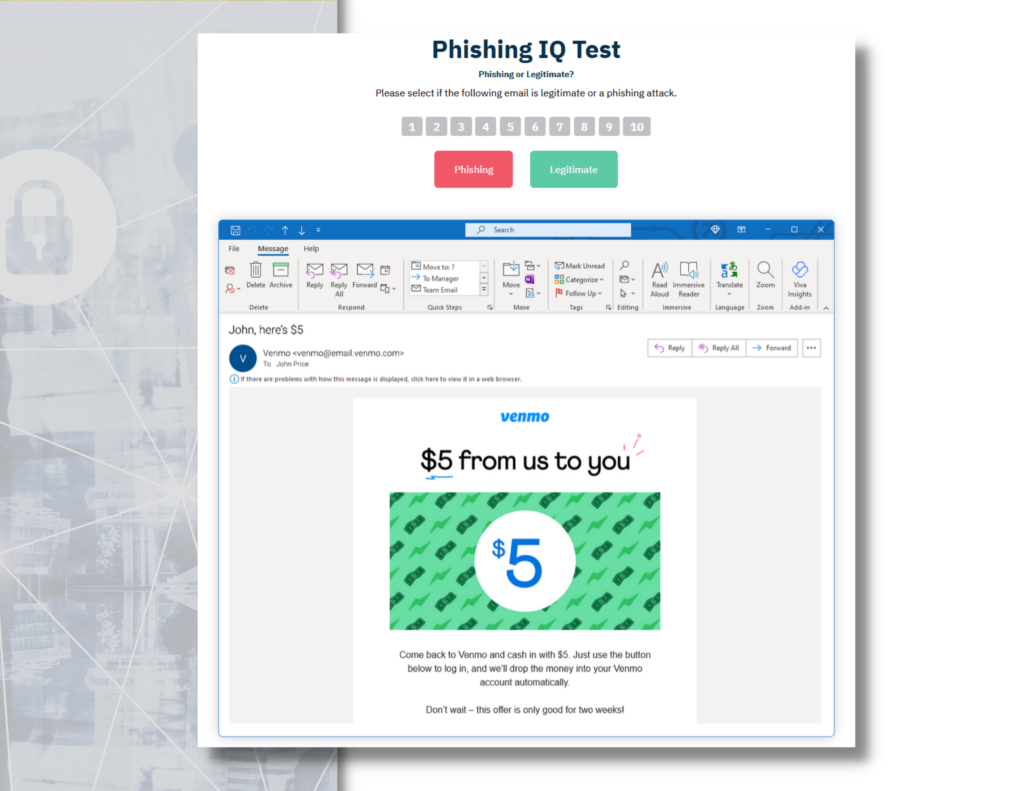
Phishing Simulations & Testing
We also do provide thorough phishing training to evaluate the effectiveness of their employees’ security awareness. Our phishing simulator is robust and allows for complex testing schedules, a dynamic template library, editing of templates, and more.
Continuing Education is Critical for CMMC
As technology continues to advance, cyber-criminals have become increasingly adept at devising sophisticated methods to gain access to sensitive information via people:
- Insider Threat
- CUI Data Protection
- Ransomware Spear Phishing
- Link Manipulation
- Smishing (SMS Phishing)
- Vishing (Voice Phishing)
- Keyloggers
- Domain Spoofing
- Search Engine Phishing
- Session Hijacking Content
- Injection

