Cybersecurity maturity model certification (CMMC)
What you need to know about cmmc compliance

CMMC and How it Impacts Your Business
If you’re in the business of selling or providing services/goods to the United States Department of Defense (DoD), it’s essential that you familiarize yourself with CMMC and establish a readiness checklist for your CMMC certification.
The Defense Industrial Base (DIB) is the target of more frequent and complex cyberattacks. To protect American ingenuity and national security information, the DoD developed the Cybersecurity Maturity Model Certification (CMMC) 2.0 program to reinforce the importance of DIB cybersecurity for safeguarding the information that supports and enables our warfighters.
The DoD has been concerned with safeguarding controlled unclassified information, often known as CUI, in its supply chain for some time and if your organization is in the DIB, you’ve probably heard plenty about DFARS. But for most companies there is still some confusion about CMMC.
Overview of the CMMC Program
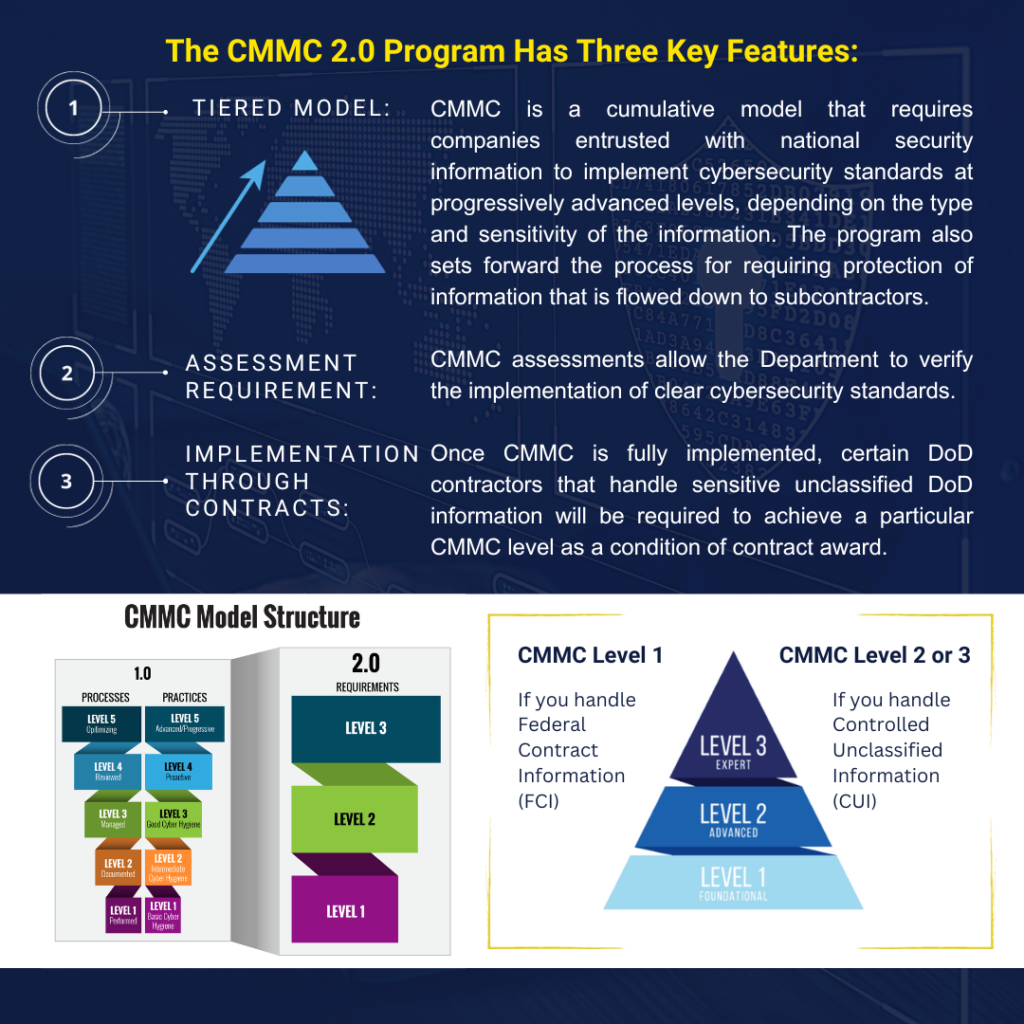
The CMMC program is aligned to DoD’s information security requirements for DIB partners. It is designed to enforce protection of sensitive unclassified information that is shared by the Department with its contractors and subcontractors. The program provides the Department increased assurance that contractors and subcontractors are meeting the cybersecurity requirements that apply to acquisition programs and systems that process controlled unclassified information.

When Will CMMC 2.0 be Required for DoD Contracts?
The publication of materials relating to CMMC 2.0 reflect the Department’s strategic intent with respect to the CMMC program; however, CMMC 2.0 will not be a contractual requirement until the Department completes rulemaking to implement the program. The rulemaking process and timelines can take 9-24 months. CMMC 2.0 will become a contract requirement once rulemaking is completed.
Who Does This Apply To?
DFARS applies to anyone doing business with the US DoD directly as a prime or as a subcontractor. The adherence to the NIST SP is required when related to handling Covered Defense Information (CDI). CDI is a broad category of information that includes:
1) Controlled Technical Information (CTI)
2) Controlled Unclassified Information (CUI)
3) Relevant information that was created for a contract (FCI)
a) This subpart applies to contracts and subcontracts requiring contractors and subcontractors to safeguard covered defense information that resides in or transits through covered contractor information systems by applying specified network security requirements. It also requires reporting of cyber incidents. (DFARS § 204.73)


CDI is used to keep in line with the CUI definition but also accounts for any future changes in the CUI Registry. DFARS § 252.204-7012(l) clarifies that CDI may also include “CUI Specific” categories of data.
CTI is specified in DFARS § 204.7301 as: “technical information with military or space application that is subject to controls on the access, use, reproduction, modification, performance, display, release, disclosure, or dissemination. Controlled technical information is to be marked with one of the distribution statements B through F, in accordance with DoDI 5230.24, Distribution Statements on Technical Documents.”
Classified CTI is subject to different requirements than those in DFARS § 252.204-7012. Its requirements are in the National Industrial Security Program (NISPOM).
