
CMMC-in-a-Box™
Your Customized Path to CMMC Compliance

Dasha Davies
CMMC CCA/SSP, CISSP, PMP, PCI-QSA, CRISC, CCISO, CGEIT, HCISPP, PCIP, ITIL, NSA IAM/IEM

CMMC Compliance
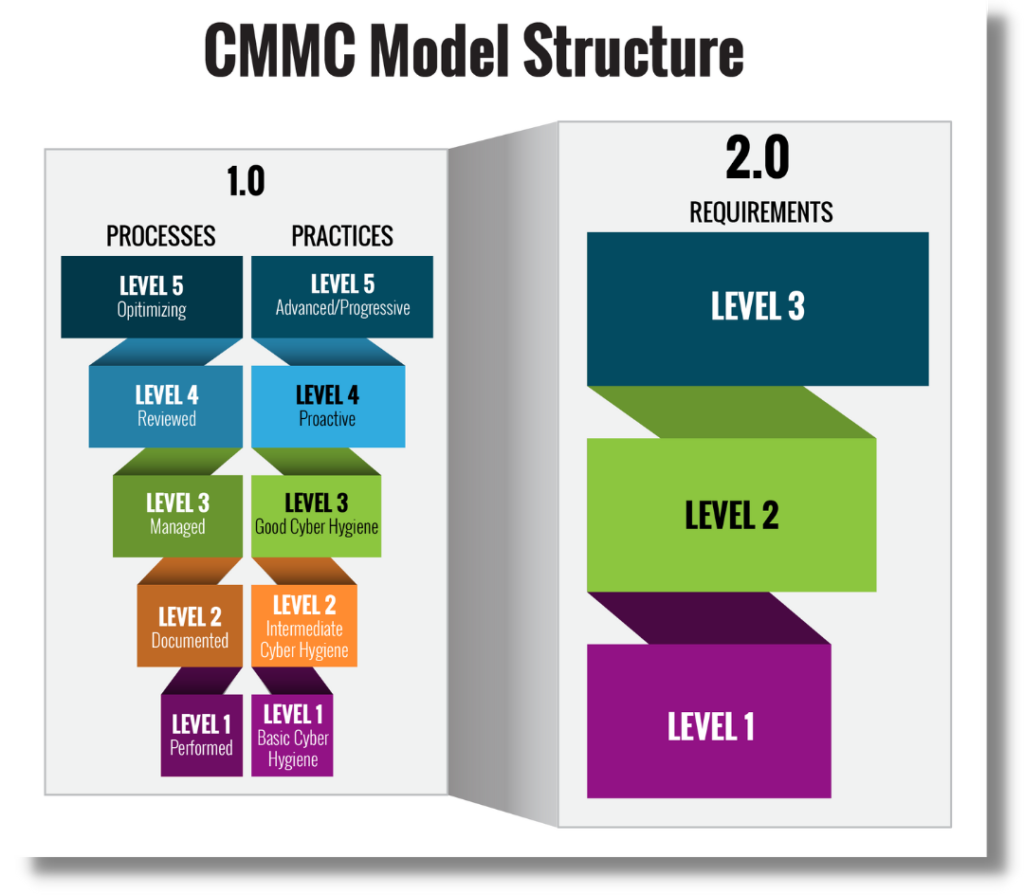
With the goal of protecting Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), the Department of Defense (DoD) created The Cybersecurity Maturity Model Certification (CMMC). CMMC is a cybersecurity standard that ALL DoD contractors will need before they can win a government contract.
Don’t risk losing out on future DoD opportunities because you’re not prepared. CMMC is about an organizational culture of cybersecurity. Setting up systems, processes, and procedures that meet the DoD standards isn’t something that you can put together overnight.
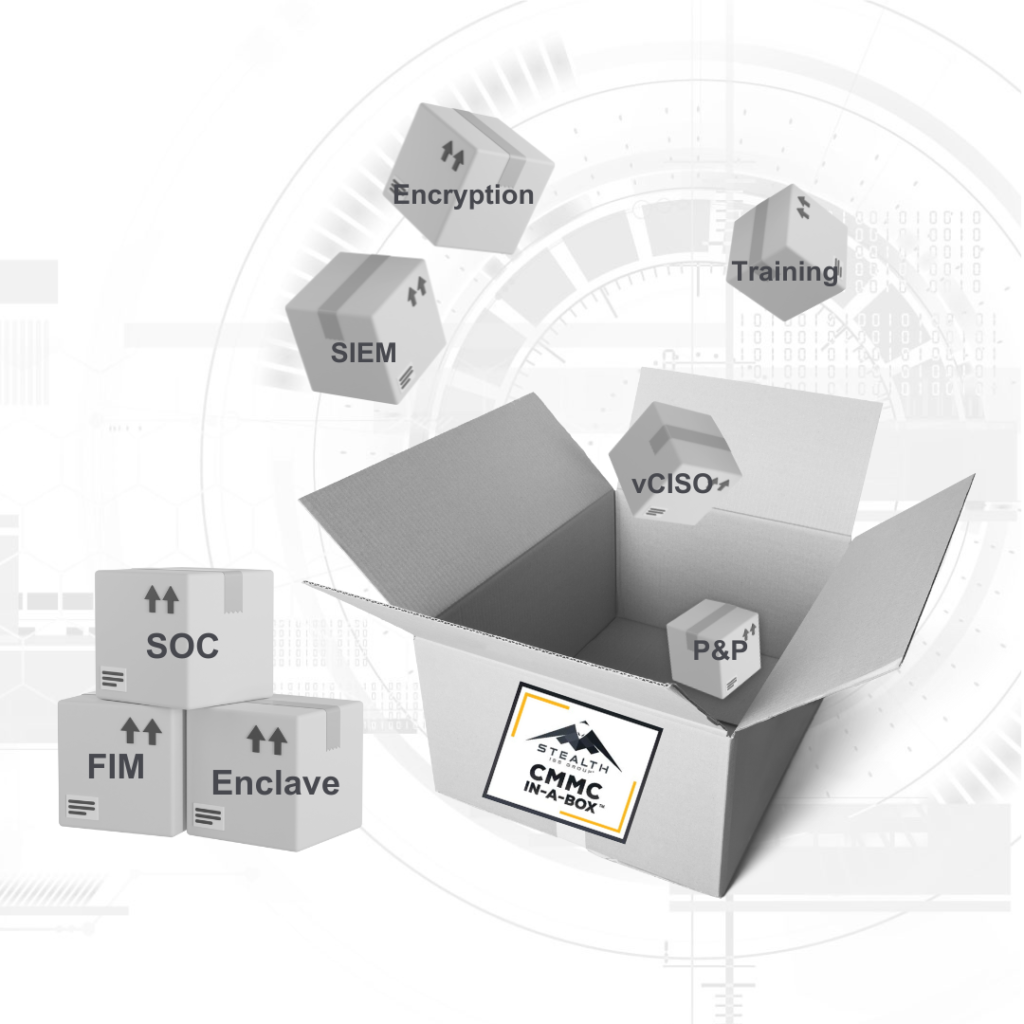
Our CMMC Packages are Tailored to Fit Your Unique Needs
At Stealth-ISS Group® we are de-risking your DoD business future with our CMMC-in-a-Box™! There is no size fits all approach to get you compliant, however we made it easier by categorizing the different security areas required for CMMC. We work on customized cybersecurity solutions and services to fit your needs and streamline the process of becoming CMMC compliant. We provide a-la-carte remediation, implementation, consulting and audit readiness.
From us you get the preparation for CMMC, while reducing the cost and effort required on the route to certification. Our team of highly certified security professionals and Certified CMMC Assessors (CCA) and Practitioners (CCP) have the extensive knowledge and experience implementing NIST and CMMC cybersecurity controls to assess your standing as related to DFARS and CMMC Requirements.
Only Pay for What You Need
CMMC-in-a-Box™ addresses security related CMMC requirements with a tailored bundle of remediation, consulting and managed security services, customized for your business, needs and operations. From gap assessments, to remediation and certification readiness.
Policies & Procedures
Cover all CMMC domains
- Mitigate risk and meet CMMC compliance
- Policy assessment and development
- Ensure security systems are being fully leveraged in accordance with CMMC
CMMC & Security Training
Your people are your 1st line of defense AND your biggest risk
- Robust phishing simulations
- Cybersecurity and Phishing Training for CMMC
- Automatic reminder and evidence collection
CMMC Security & Risk Assessments
Identify weaknesses in your security posture
- Tailored advice on how to secure your data and network and meet CMMC compliance
- Reduce your risk of breach
- Identify and remediate the gaps between your current setup and CMMC
Remediation
Custom Service Bundling
- We will help build a plan and close your existing gaps while formalizing your processes, controls and documenting your compliance.
- End-to-end solutions for DIB clients needing CMMC assistance
SOC-as-a-Service
24/7 Security Operations and Incident Response (IR)
- Complete 360 degrees of managed cybersecurity and SOC
- Monitoring & Control
- Prevention & Detection
- Response Orchestration
SIEM-as-a-Service
24/7 Monitoring & Log Management
- General admission and member discounts for two adults
- Five free tickets per special exhibition
- Six single-use guest passes per year
Email Encryption
Military-grade encryption and ransomware protection
- End-to-end encrypted file storage and sharing
- Encrypted email
- Designed to support CMMC compliance
- Encryption Key Management
- CMMC, NIST 800-171 & ITAR compliant
CMMC Enclave
Modernize your mission-critical processes, meet CMMC compliance
- Top-tier, built-in security and government cloud compliance for unclassified data (FCI/CUI) and workflows
- Attain a Zero-Trust architecture
- Ensure security and CMMC compliance
File Integrity Management (FIM)
Provides a clear and simple method to implement many of the control objectives of CMMC
- Operate with the highest security standards 24/7 with a fraction of the effort
- Achieve a continuously compliant infrastructure
- Mitigate your risk of security breaches in real-time
Vulnerability Scanning & Penetration Testing
Proactively detect vulnerabilities and protect against cyber threats
- Critical asset protection with managed scanning
- Provides visibility into your network
- Identifies the gaps
- Reporting aligned with CMMC standards
Multi-Factor Authentication (MFA)
Quickly and securely verify trust
- Confirm user identities in a snap.
- Monitor the health of managed and unmanaged devices.
- Set adaptive security policies tailored for your business.
- Secure remote access without a device agent.
- Provide security-backed, user-friendly SSO.
vCISO (CCA/CCP)
Your Dedicated security and CMMC compliance experts
- Have your CMMC CCA in-house to manage your CMMC program
- Perform gap analysis and readiness assessment
- Guide your team with remediation and evidence colelction
- Create a custom strategy and prioritization for you

Work with the Experts
Dasha Davies, CCA herself was one of the first 25 people chosen to be trained on CMMC requirements, methodology, scoping and consulting. That was in 2020. Since then she has been working with many defense companies on a daily basis to answer their questions, help them become compliant, remediate issues and close the gaps, and get them ready for the official CMMC certifications.
As a U.S. Veteran and thought leader for various Fortune 100 and 500 organizations, small and mid-size businesses and even the US government, Dasha is uniquely qualified to help you and your business comply with the stringent requirements put in motion by the DoD.
Start your cmmc compliance journey by talking to our experts
Schedule Your Complimentary Consultation Today!
