File Integrity Monitoring (FIM)
Continuous Security & Compliance
Get compliant, stay compliant, and prove it.
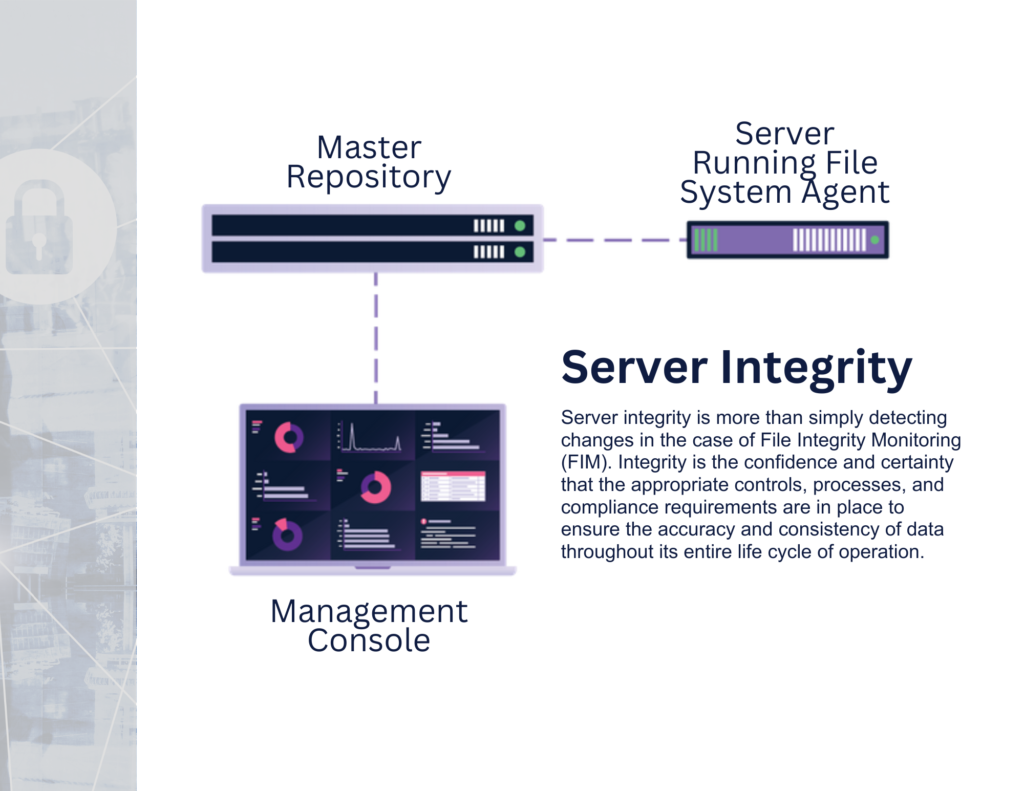
Total File System & Device Integrity Monitoring
Detecting changes in your IT environment, and being able to respond to them quickly, is a critical component of a solid cybersecurity program. To ensure that your business operations are always available and performing as expected, it’s vital to adopt a comprehensive security, integrity and compliance solution.
Our Managed Continuous Security & Compliance with File Integrity Monitoring Security Service is a powerful compliance, information assurance, and security solution for your business. We provide you with a comprehensive set of security, auditing, and compliance solutions to ensure the integrity of your entire IT Infrastructure.
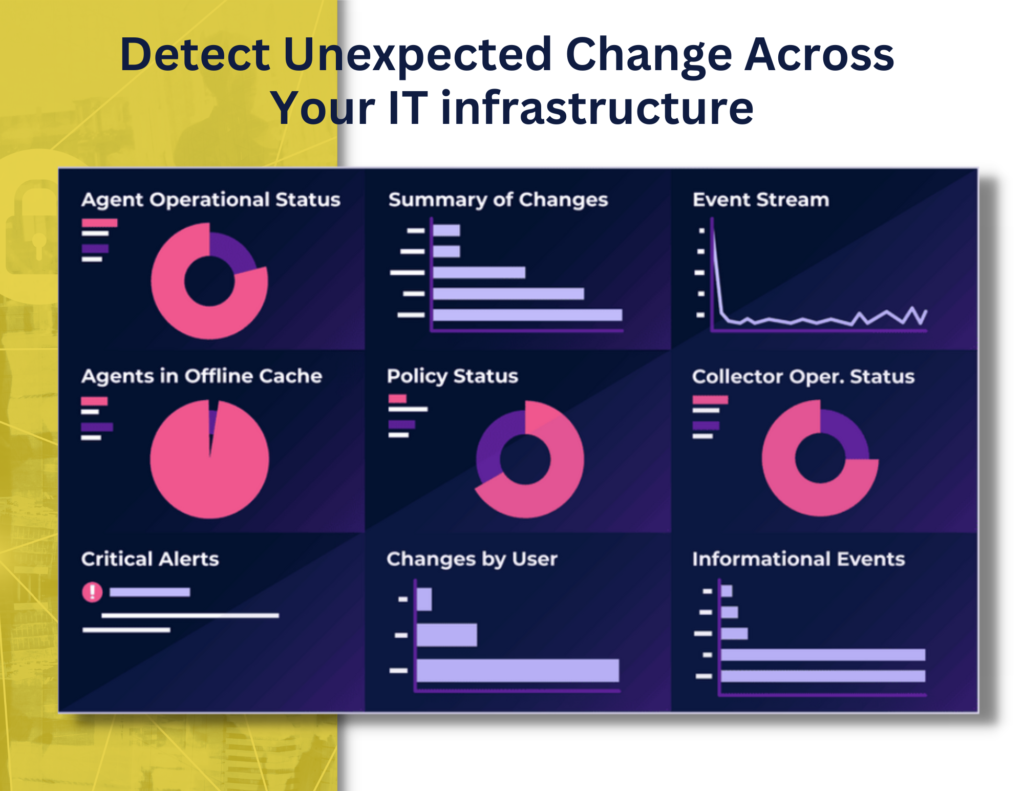
Detect Changes to Critical Files
Detect zero-day attacks and unauthorized changes in real-time, while simultaneously complying with regulations such as PCI-DSS, HIPAA, NERC, and FISMA.
With our File Integrity Monitoring services, we can detect changes to critical files including system, application, and configuration files. Monitor registry, installed software, local users/groups and more.
We’ll detect zero-day attacks and unauthorized changes in real-time, while simultaneously complying with regulations such as PCI-DSS, HIPAA, NERC, and FISMA.

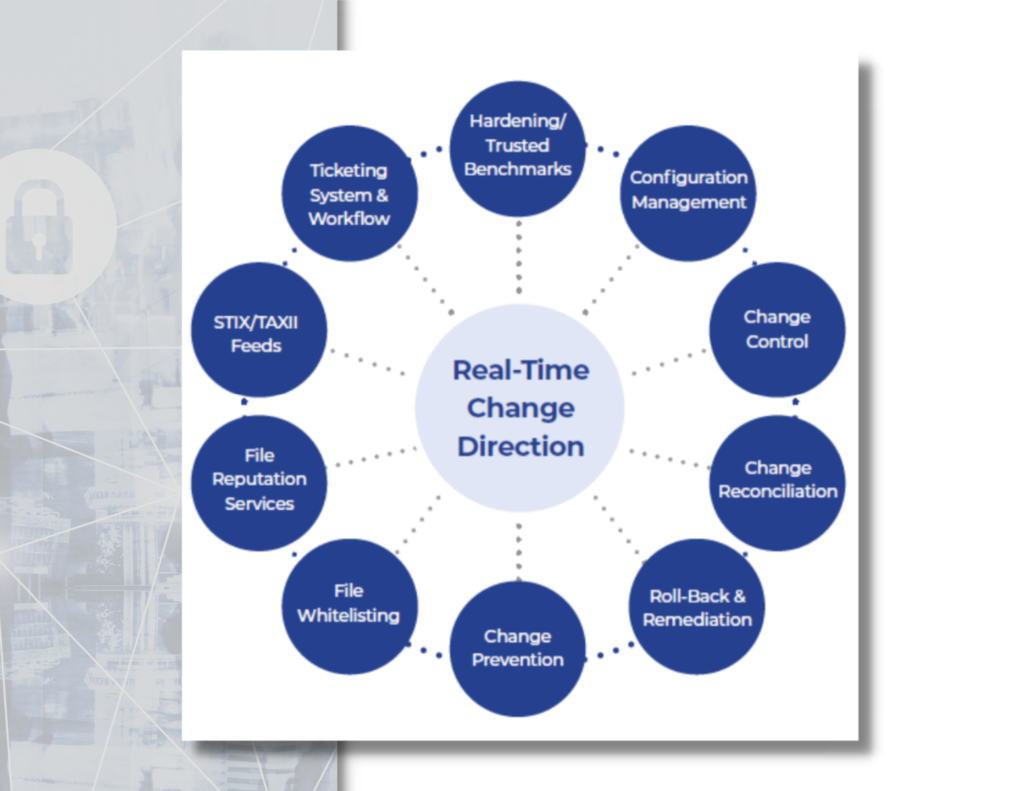
Maintain a Secure State
We protect you against external attacks that slip by your firewall or intrusion detection system.
We provide you with complete visibility, and be able to identify and respond to internal threats originating from inside the network or even the occasional accident by IT personnel.
Plan Any Change with Integrated Ticketing
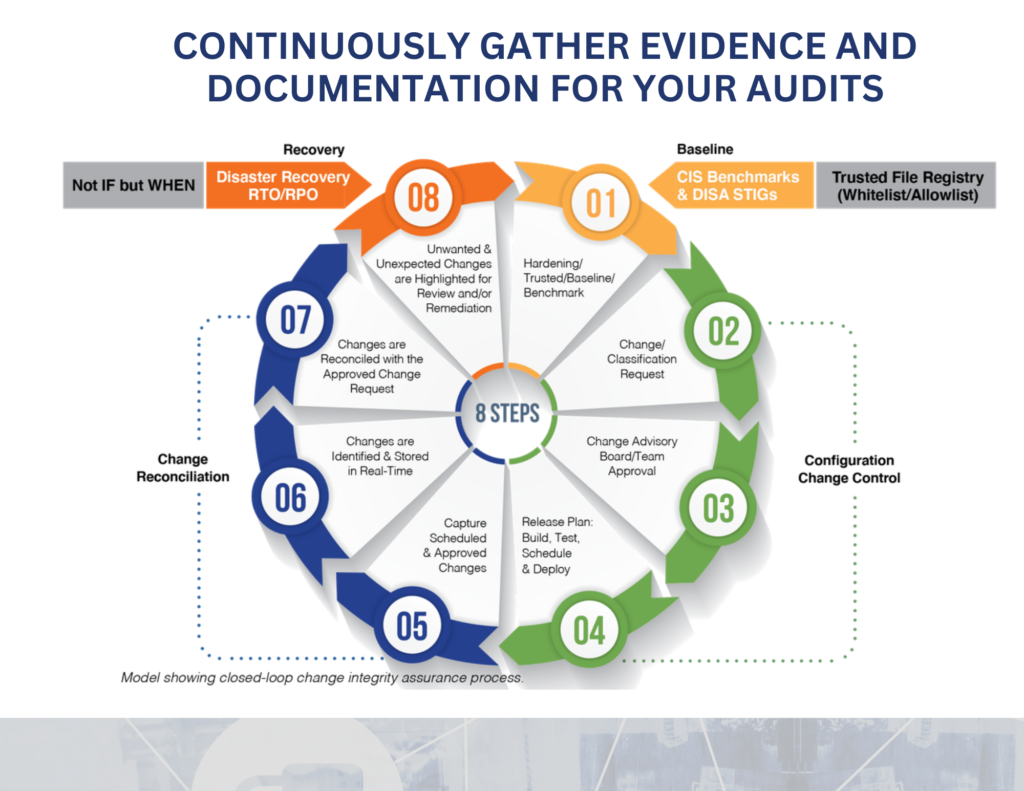
We automate the detection and documentation of all changes within the IT infrastructure. This simplified process for creating and dynamically updating authoritative baselines saves time and resources.


Automatically Identify Changes Due to Patches and Updates
Our managed services gives you with the ability to automatically identify changes due to patches and updates.
Ensure the integrity, security, and compliance of all critical components within your IT infrastructure

WORKSTATIONS
We protect you against unauthorized change to workstation/desktops with specific functionalities or those running critical applications. We monitor all of the same items for servers, but scaled to meet the needs of the smaller machine using minimal system and network resources.

DATABASES
We protect you against unauthorized changes to critical database schemas including changes to security and access settings which have the potential to allow critical data to be breached.

SERVERS
We protect you against unauthorized change to vital applications and servers (physical, virtual or cloud-based), including operating system settings, system files, directories, data files, file attributes and Windows® Registry settings.

POINT OF SALE (POS)
We protect you against changes to POS systems that can allow payment card data to be breached or cripple these business-critical IT assets.

ACTIVE DIRECTION / LDAP
We protect you against changes to your directory services including objects, attributes, and schema.

NETWORK DEVICES
We protect you against unauthorized and destructive changes to your network infrastructure, including firewalls, routers, and switches as well as accidental misconfigurations that can lead to your IT infrastructure being compromised.

VMWARE/ESXI
We protect you against changes to VMware ESX and ESXi host configurations that can lead to a compromise of a large number of “guest” virtual operating systems.